Hey all,
Currently securing our server and have implemented the following ruleset which should work:
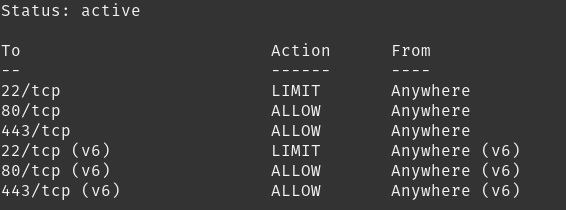
However when doing so, and looking at the technician console, online machines start disappearing and im left with everything appearing offline. Disable UFW and its back to normal. Any ideas? Cheers!
I use CSF.
You need to allow UDP as well if your assets use UDP.
If your SSH port is still 22. I would change that as well.
Also if your using DigitalOcean / Hetzner you can use their firewall for extra protection.
In CSF you have a deny list. I denied all TOR IP’s
yes, as @Jayjayuk said you need the udp ports open for 443 and 80 ( https://simple-help.com/public-accessibility-guide )
Also with having ssh make sure you are running fail2ban (or something similiar), and I’d also reccomend you are running unattended updates (if it’s ubuntu here’s the guide - https://help.ubuntu.com/community/AutomaticSecurityUpdates#Using_the_.22unattended-upgrades.22_package )
Personally, I disable ssh via firewall until I need it for added security. I only use it for doing simplehelp or server upgrades anyway.
Simplehelp defaults to udp for clients, but you can change that in the config file so that it uses tcp. That way if you don’t want to open up udp you don’t have too. You will need to make sure your clients are switched over first though.
@Darrell_Swafford - I can’t think of a scenario where you you would be able to disable/enable an ssh firewall rule, where you wouldn’t already have console access, so why not just do your updates/upgrades that way without ever enabling/disabling ssh firewall?
SSH configured with root login disabled and using keys, or a very strong unique password paired with fail2ban is more than sufficient. In my 17 years of managing publicly accessible linux servers this has never been an issue, nor have I heard of it being one. (this also assumes that you are applying security updates regularly/automatically)
I don’t see much reason to turn off udp, as if you think it is insecure than tcp would be just as vulnerable, so why not leave them both open as it expects?
SimpleHelp’s suggested config:
If the machine you are sharing can access your server over UDP then we would recommend using it as it is more scalable. A SimpleHelp server can support more machines connecting over UDP than over HTTP. If you have thousands of shared remote access machines then using UDP for at least the bulk of them is a must.
Sorry I may have misread the original reply. I have the firewall separate from the server for more granular control.
Thanks all,
Taken onboard points, have it now working, and have UFW, Fail2Ban, 2FA and automatde updates happening.
1 Like
thanks for the tips. Re the auto updates, have you had issues with this? Ive heard many say this is crazy enabling this on a linux server. Thoughts and exeriences here? Cheers!
1 Like
We have all of our linux servers doing auto updates for security updates. This should never affect anything at all that Simple-Help does as Simple-Help brings it’s own stack. We not only have it downloading security updates automatically, but also installing them and rebooting overnight if needed all automatically.
We’ve never been advocates of holding back or babysitting updates, we have the same policy in place for all of the windows computers and servers that we manage (most people will think this is insane for some reason) - I’m sure there are special cases out there, but having all machines check for updates daily, and apply them daily, and reboot automatically overnight has yet to bite us. With all of the zero day vulnerabilities, and the ability for malicious actors to reverse engineer updates within minutes/hours and get exploit code out there these days the benefits outweigh the potential risks. Most people that would balk at this either have special cases that they can’t do it, or more likely, are stuck in old school thinking where you would be very careful about updates as they could sometimes brick the os. That just doesn’t cut it in the current security climate we are in. (of course this is all my opinion, but I do have some experience with these types of things)
Brilliant. I agree wth this line of thikning but wanted to chekc with you as it sound slike youve been patching linux automatically a lot longer than most! Appreciate the feedback.
1 Like


 Remote Support
Remote Support Remote Access
Remote Access Monitoring and Management
Monitoring and Management Presentation
Presentation Remote Work
Remote Work Standard
Standard Business
Business Enterprise
Enterprise