Hello All…So I have been using the script below in a toolbox for patching devices and it works quite well…However, I am looking for other options that can be deployed that will give more results of the patching either via email or logs in some fashion. Even though this script works well it does not provide any details as to what is done, etc. I have not played with ABCupdate yet and I assumed the use of PSWindowsUpdate below would eliminate the need for it. I am just trying to query the group as to how they are doing things via SH. Also, what is annoying is that even after this script goes through the alert still sticks around saying there are updates required. Thanks all
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
Set-ExecutionPolicy -ExecutionPolicy Unrestricted -Scope Process -Confirm:$False -Force
If(-not(Get-InstalledModule PSWindowsUpdate -ErrorAction SilentlyContinue)){
Install-PackageProvider NuGet -Confirm:$false -Force
Set-PSRepository -Name ‘PSGallery’ -InstallationPolicy Trusted
Install-Module PSWindowsUpdate -Confirm:$False -Force
}
Import-Module PSWindowsUpdate
Get-WUInstall -Install -AcceptAll -AutoReboot -MicrosoftUpdate
I was using the built in os updates notification linked to abc-update, but the issue was that there was no easy way to see what updates a device had or when.
In the end I decided to run Syncro in the background to manage updates, 3rd party updates and install admin account, encrypt drive and backup the key. I still find myself using simple help for ease, but Syncro gives me the reports and evidence things are happening.
I have been onto support for years about patch management, but nothing yet.
Thanks for your information. I am really trying to mitigate the attack surface but minimizing the tools I am using for remote management so I am hoping to find something SH can do without layering another tool at this point.
I really appreciate your reply…
Hi Mike,
No worries. sorry it wasn’t the solution you were looking for, but if you find something, please let us know.
So far I have used ABC-update and rzget for 3rd part patching.
So I have not done this yet, but want too. Maybe I can work on it later in the week.
I am going to use the Built-in Simplehelp alert to check for updates.
Have the trigger run a script that runs PSWINDOWSUPDATE Get-WUList
Use the Scripting API to dump the update list to “ServerUtilsSetMachineProperty” with a timestamp, (Could also do a log or email. ) that way I know what was updated.
Then run the install at a time when the machines not used.
Get-WUInstall -Install -AcceptAll -AutoReboot -MicrosoftUpdate
Could also send the output the machine property with a time stamp.
Make sure the alert threshold is set to reset the trigger, or just to be sure, use the scripting api and set this in the script: “ServerUtils AlertReset”
Thanks for the reply…Now that looks like a good project…I might take a poke at it this week as well.
Much appreciated
So Here is what I came up with.
Test it out let me know what you think and ways to improve.
Hope it helps.
Powershell script:
#set execution policy for powerhsell
Set-ExecutionPolicy Bypass -scope Process -Force
#set tls 1.2
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
#check for pswindowsupdate module. Install if not all ready installed.
If(-not(Get-InstalledModule PSWindowsUpdate -ErrorAction SilentlyContinue)){
Install-PackageProvider NuGet -Confirm:$false -Force
Set-PSRepository -Name ‘PSGallery’ -InstallationPolicy Trusted
Install-Module PSWindowsUpdate -Confirm:$False -Force
}
#import module for use
Import-Module PSWindowsUpdate
#Get list of available updates
$PSWULIST = Get-WUList
#store list on machine property so we know what got last installed
ServerUtilsSetMachineProperty(@ThisMachine(), Last Windows Updates, $PSWULIST)
#Install updates, but dont reboot
Get-WUInstall -Install -AcceptAll -MicrosoftUpdate
#Check if update required Reboot, write it to machine propertys
$PSWUREBOOT = Get-WURebootStatus |Select RebootRequired, RebootScheduled
ServerUtilsSetMachineProperty(@ThisMachine(), LastUpdate Reboot Required, $PSWUREBOOT)
#reset SimpleHelp Alert
ServerUtils AlertReset
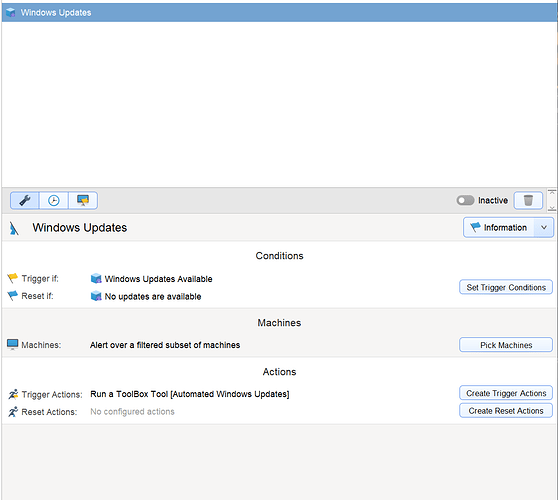
And Alert Settings:
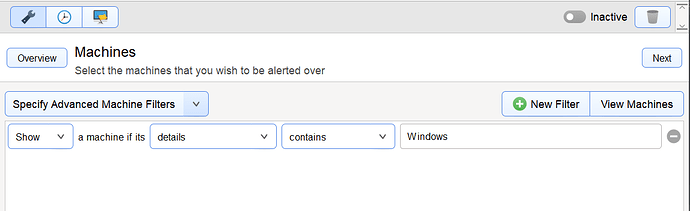
Filter windows only devices:
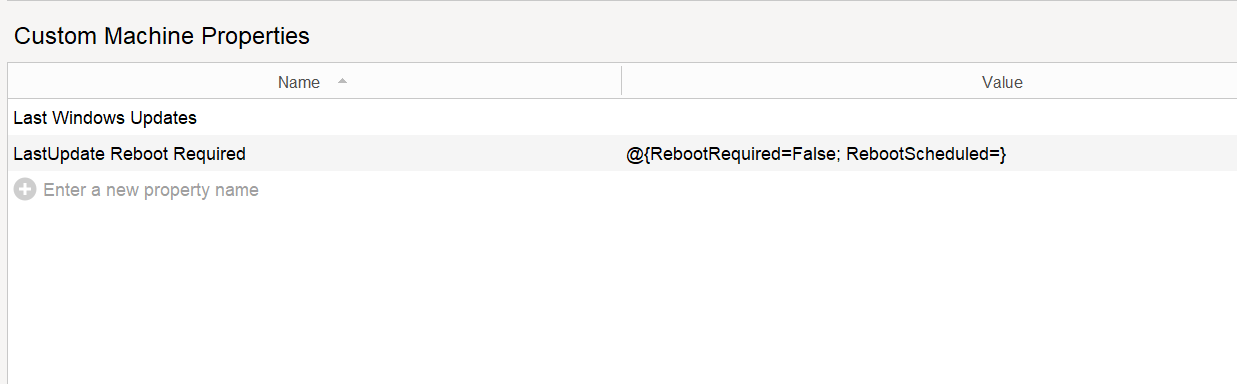
Machine Property’s the script adds.
2 Likes
Interested to hear if others prefer to just let WindowsUpdate do a blanket update of Drivers or do you use something a little more restrictive like below?
Interested to see if everyone believes Windows Updates is mature enough now to handle end device Driver updates without check?
Instead of using
#Install updates, but dont reboot
Get-WUInstall -Install -AcceptAll -MicrosoftUpdate
Was wondering if better to use:
Write-Output “Install Available Updates - Not Drivers - No Reboot”
Install-WindowsUpdate -NotCategory “Drivers” -AcceptAll -IgnoreReboot
Also, if Systems are using .Net 4.7 or above, would you not be changing default of trying TLS 1.3 and forcing to use TLS1.2 only ?
 All Good Points @Rod_Arthur
All Good Points @Rod_Arthur
Should be able to script a check .net
On my WSUS systems I dont usually do drivers. On the home systems I have taken care of, I have noticed that they have gotten better. So if you have a system to take care of the drivers I would say
ignore them. If not maybe let them update ? Ignoring the reboot is a good practice for this type of check otherwise it would most likely interrupt somebodys work.
It maybe a good idea to setup a separate SimpleHelp alert and check if a reboot is needed and then force a reboot on off hours.
1 Like
@Darrell_Swafford - My first dabble to use Toolbox Scripting API cmdlets. So I likely doing something wrong
I am trying your script but have the following Custom Machine Properties values which I am sure is not what your one looks like? What am I doing wrong?
7134136509669618402123_SCRIPT_APIServerUtilsSetMachineProperty(@ThisMachine(),“Last Windows Updates”,“System.__ComObject System.__ComObject System.__ComObject System.__ComObject System.__ComObject System.__ComObject”)SCRIPT_API_9332386195324441315379
7134136509669618402123_SCRIPT_APIServerUtilsSetMachineProperty(@ThisMachine(),“LastUpdate Reboot Required”,“@{RebootRequired=False; RebootScheduled=}”)SCRIPT_API_9332386195324441315379
So I think I know what the problem is.
The Machine Property apperas to only accept a single line and we are outputting a multi-line table with Get-WUList
Not sure exactly how to do it, but I think its something like this:
$PSWULIST = Get-WUList | Select-Object -Property Result , Title ; -join '; '
Hopefully someone is better with PowerShell that has suggestions 

 Remote Support
Remote Support Remote Access
Remote Access Monitoring and Management
Monitoring and Management Presentation
Presentation Remote Work
Remote Work Standard
Standard Business
Business Enterprise
Enterprise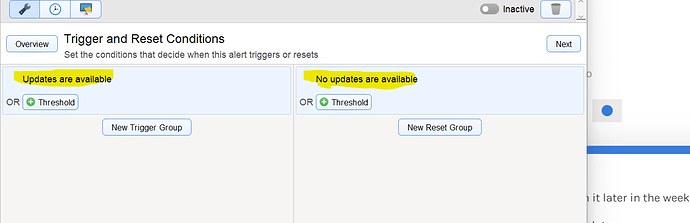
 All Good Points
All Good Points